HackTheBox: Open Admin
Welcome to my first write up in HackTheBox Open Admin machine this is also my first machine.
So let’s jump in!


Start with the classical Nmap analysis:

- sS for TCP Syn scan
- sC for default scan script
- -A for Version detection and OS Detection
- -p- for all ports scan 0 to 65535
Since I already have the nmap result, so let’s view our nmap.txt

We have port 22 (SSH) and port 80 (HTTP). Port 80 is the port number assigned to commonly used internet communication protocol, Hypertext Transfer Protocol (HTTP), it’s just simply a Website. Let’s take a peek on this HTTP website.

As we can see, we have the default Apache2 website.
I tried fuzzing the website from the root domain with wfuzz tool and dirb for further enumeration.


So we discover sub directories in http://10.10.10.171/



By viewing those website only one website that leads me forward: http://10.10.10.171/music, I quickly notice the “Login” button in http://10.10.10.171/music, this button leads us to http://10.10.10.171/ona which is didn’t appear in my fuzzing earlier. ONA stands for Open Net Admin.
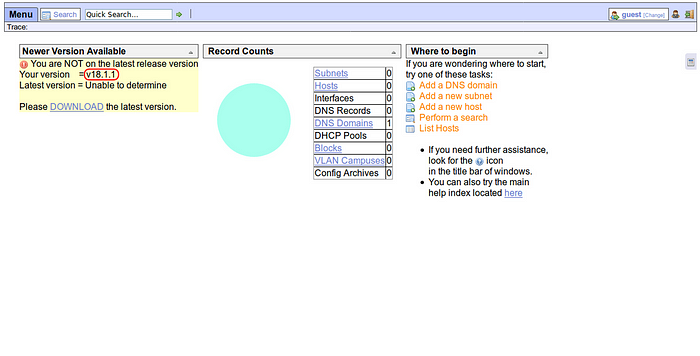
ONA version v18.1.1
By searching it to Google, ona v18.1.1 has an available exploit.


So, I copy this exploit.

So let’s fire up this exploit script and wait for the result.

Awesome I’ve got a low-privilege shell. Very low that you can’t even change your directory.


but the good thing is I can use “ls” command to list all folders in my current directory. Using “ls” I can look up files into the other directory without leaving in my current working directory.
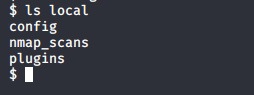



It seems to be a MySQL database Credentials. I tried to log in this in mysql using my low-privilege shell but it doesn’t work. So I need to enumerate further in this machine.
by taking a peek at /etc/passwd folder, we get some useful information which is the users of this machine. Joanna and Jimmy.

After days of head banging in this machine, I’ve got a hint from my friend of mine that one of the users can log in thru SSH using MySQL Credentials.
So I quickly tried jimmy:n1nj4W4rri0R!

Finally I have a proper shell!
By using the Mysql Credentials ona_sys:n1nj4W4rri0R! I am able to log in mysql and do some enumeration on it.



Inside the users table, I’ve obtain the Admin’s Credentials. Copy the password hash and identify what kind of hash using hash-identifier.

So it seems that this hash is MD5, so I search online MD5 Decoder.

Hash has been decoded and we have the plain password. Username: admin, Password: admin. So, what now??
In further enumeration, in /var/www/internal/ folders, I viewed some php codes.

Just view one of the php codes (main.php).

if I able to run the main.php, this codes will show Joanna’s Id_rsa which is a Private RSA Key but how?? another hint from my friend that I can use curl command together with the credentials of admin:admin in the localhost.
Searching for the right port using netstat.

using 127.0.0.1:52846, we gonna run our request together with the admin:admin credential.
curl -u admin:admin http://127.0.0.1:52846/main.php

It works! We obtain the Private Key for Joanna, So I copy this Private key to my folder.
I convert the Private Key first into hash using ssh2john.
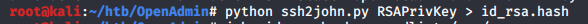
using JohnTheRipper for cracking the converted Private key id_rsa.hash.

Cracked finished, so I get the plain password which is “bloodninjas”.
Using this password, I can connect thru ssh using Joanna:bloodninjas.

now I have Joanna’s shell, I am able to view the user.txt.

Now I am aiming for the ROOT privilege.
Let’s do the enumeration again. Using sudo -l,it will show a list user’s privileges or check a specific command.

we can use command “nano” without using administrator/root passwd.
nano is a popular command line text editor that is included in most Linux distributions.
But how can we use this to escalate our privilege?
Upon searching on Google, I came up to this site. https://gtfobins.github.io/
since I have the privilege of using nano without using root password, I’m using this to escalate my privilege.


Let’s do this, fire up the nano.

Then press CRTL+R and CRTL+X



inserting the “ reset; sh 1>&0 2>&0 “

Code Executed and Rooted, so I quickly grab the flag in /root folder.

Thanks for reading guys I hope you learn something in my first machine in Hackthebox. Peace :)

