Castor CTF 2020
Sat, May 30, 04:00 — Mon, June 01, 04:00 PHT

Team: p0isonP4wn
Forensics: Manipulation

I find this forensics challenge interesting, since it brush up your Linux command skills. So, let’s get started.

So this challenge includes a JPEG file that I already downloaded.

when I open the JPEG file it doesn’t show an image, seems that it is a corrupt file.

so I try to check this file by file command and shows that this file is a ASCII text. It seems suspicious since this must be a JPEG file.

checking file again by using strings and it shows a hex dump.



I quickly notice the last line of hex dump since it is FF D8 FF E0 and that hex is a File Signature of JPEG. It seem that the first line of hex dump was intentionally put into the last line.

Note: FF D8 FF E0 head file signature and FF D9 is the tail.


So I did a little repair of hex dump in text editor.

Since I have the right hex dump here, my goal is to reverse compile this hex dump by extracting hex dump itself.

using cut command, we gonna trim out those unwanted text and extract what we want.




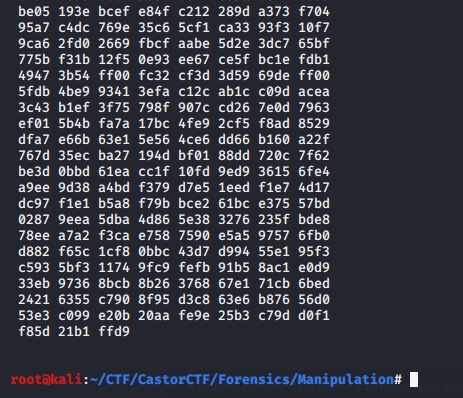
Now we need to remove all spaces and lines.


now we will reverse compile this hex dump using “xxd”.



Flag: castorsCTF{H3r3_Is_y0uR_Fl4gg}
I apologize for my methods, I’m still noob.
Forensics: Leftovers

This challenge gives us an interesting capture of data.
Take a look at wireshark

this might be a USB packet capture (keyboard strokes), I try to extract those Leftover Capture Data using tshark.

using this on table (page 53), we are able to decipher those hex with corresponding data values.

I use this python script https://blog.stayontarget.org/2019/03/decoding-mixed-case-usb-keystrokes-from.html which is a write up with similar in this challenge. ( Credits to the owner )

Flag: castorCTF{1stiswhatyoowant}
Coding : Arithmetics

In this challenge, we need to connect thru netcat and solve a simple math but we need to be fast (literally fast) or else the netcat will close.

We need to automate this our connection first in netcat using python.

then we gonna test this out first.

Seems it working, what I do next is to remove the extra strings in question that has given to us. So simply remove the “What is” and “?” then we left the “9–3” thingy which is needed for eval() function.

We gonna test it again.

Seems our code is working and get another question, So I simply copy and paste the code to repeat the process. (I humbly apologize for my method in this challenge, this is my first time to write script in python. Peace)


After many copy and paste, I encountered some questions that the given question is in form of strings, just like “one + 1” ,“ one multiply-by six”, “six plus nine” and so fourth.

I just run and wait for the flag to show up, until I get the flag.

Wow! You’re fast! Here’s your flag: castorsCTF(n00b_pyth0n_4r17hm3t1c5}
Flag: castorsCTF(n00b_pyth0n_4r17hm3t1c5}
This challenge is an achievement for me since this is my first python script.
Thanks for taking time to read.









